In today’s digital age, cyber security is not merely an option but a necessity for any organization looking to thrive in an increasingly hostile threat landscape. At Simpl Technology Solutions™, we are your trusted partner in navigating these challenges and fortifying your digital fortress against cyber threats.

Prevention
This focuses on implementing measures to prevent cyberattacks from occurring in the first place. This includes measures such as firewalls, antivirus software, intrusion detection systems, access controls, and security policies and procedures.
Detection
Detection is the ability to identify when a cyberattack or security breach has occurred. This includes technologies such as intrusion detection systems, event management (SIEM) systems, and endpoint detection and response (EDR) solutions.
Response
Once a cyberattack has been detected, it’s crucial to respond quickly and effectively to minimize the impact and mitigate further damage. This involves having incident response plans and procedures in place, as well as tools and processes for containing and neutralizing threats.
Recovery
The final pillar of cybersecurity is recovery, which involves restoring systems and data to a secure state after a cyberattack or security breach. This includes restoring backups, patching vulnerabilities, and implementing lessons learned to strengthen security posture for the future. Additionally, it involves conducting post-incident analysis to understand the root causes of the attack and prevent similar incidents in the future.
Only 14% of small and medium sized businesses have some form of protection in place.
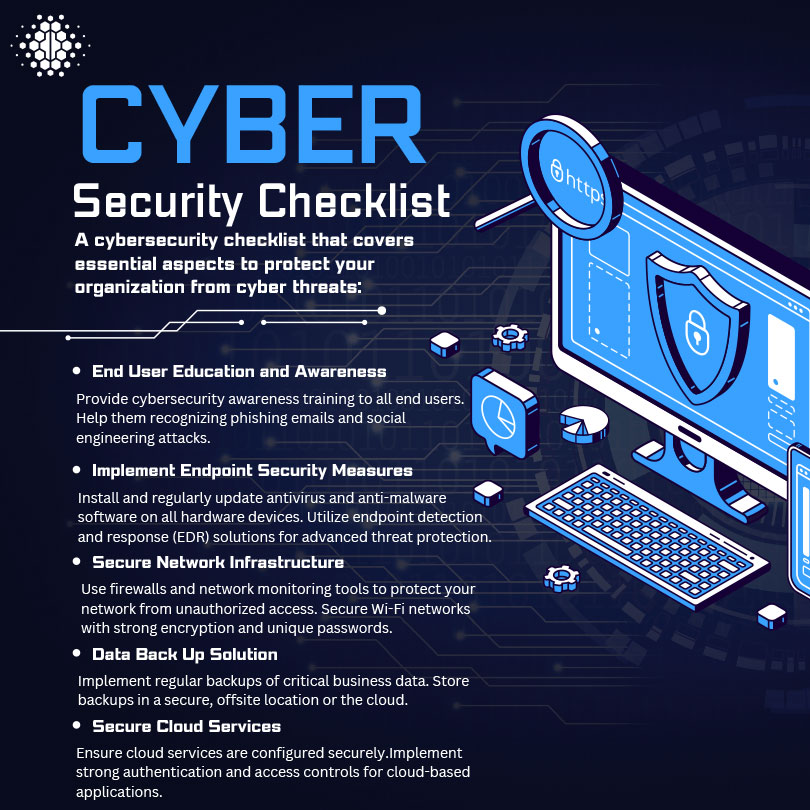


We provide incident and breach response that supports your team in all scenarios, and we automatically take action to stop any malicious or anomalous activity on a your behalf. We have the ability to tune pre-approved actions in our your company portal to match your risk appetite.

Cyber incident response, often referred to as incident response (IR), is a structured approach to managing and mitigating the aftermath of a cybersecurity incident. Such incidents can include data breaches, malware infections, denial-of-service attacks, unauthorized access, and other security breaches that compromise the confidentiality, integrity, or availability of an organization’s information systems and data.


Identify and confirm the occurrence of a security incident. This involves monitoring network traffic, system logs, and other security tools to recognize abnormal or malicious activities.

Isolate and minimize the impact of the incident to prevent it from spreading and causing further damage. This might involve blocking network traffic, isolating affected systems, or revoking compromised credentials.

Identify the root cause of the incident and remove the source of the attack. This can involve removing malware, closing vulnerabilities, or eliminating the compromised access points.
POWERED BY A SECURITY OPERATIONS CENTER TEAM OF TRAINED EXPERTS

A Security Operations Center (SOC) is a centralized function staffed by expert cybersecurity analysts whose sole function is the monitoring, reporting, and (sometimes) remediation of cybersecurity incidents, most often data breaches.
The security experts that comprise the SOC are typically well-trained analysts that are well-versed in threat detection, threat hunting and generally possess excellent cybersecurity skills.
POWERED BY A SECURITY OPERATIONS CENTER TEAM OF TRAINED EXPERTS
Compared to the in-house SOC option, the cost-value benefit of an outsourced SOC partner is immense.

Open Hours:
Mon – Fri: 9:00 am – 5:00 pm
Copyright © 2024 Simpl Technology Solutions™