-
Feb, Mon, 2024
Home
-
Your I.T. Managed Services & Cyber Security Service Partner
From device purchase and management up to device monetization, we help organizations simpl™-fy it all.
-
Trusted Cyber Security Solutions for Your Organization
We specialize in providing end-to-end I.T. services. With a client-centric approach, we prioritize understanding your unique requirements to craft a solution that fosters growth, security and efficiency.
-
Device Value Optimization
As your organization’s devices come to their end of life cycle and you refresh to newer equipment we are here to help ensure that you get the best value possible for your old equipment.
Simpl Technology Solutions™ for You
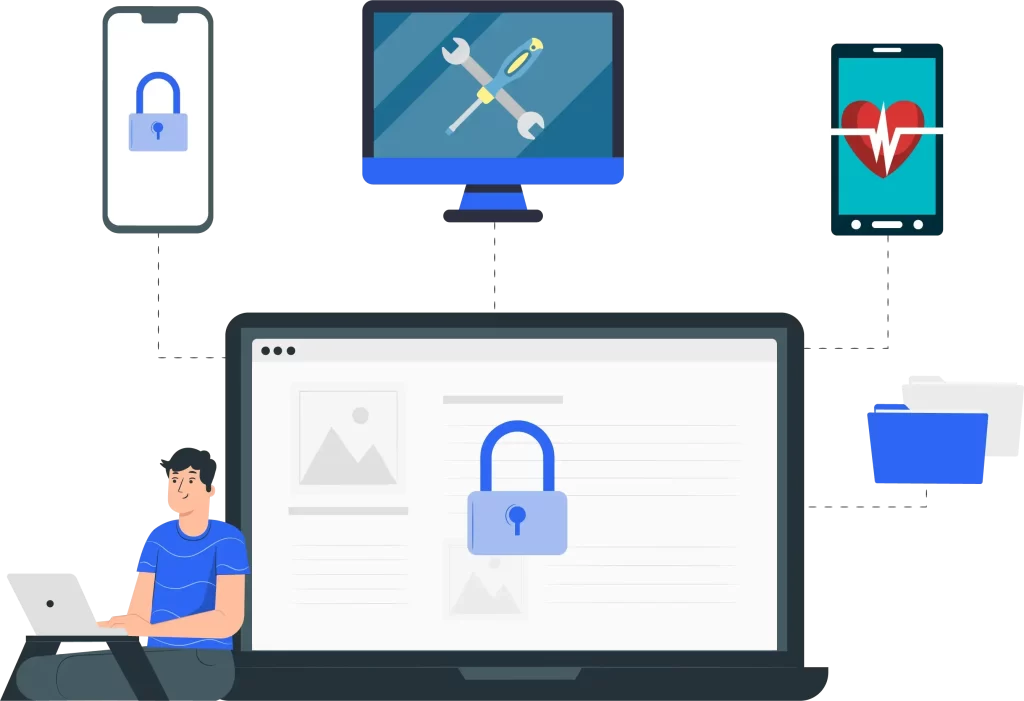
Cyber Security
Management
Cyber Security helps protect sensitive and valuable information, including personal data, customer data, financial records and intellectual property. Breaches can lead to theft, identity fraud, financial losses, and other forms of harm to your business.
LEARN MORE ▸
Unified End-Point Management
UEM is a comprehensive approach to managing and securing all devices or endpoints within an organization. UEM solutions aim to streamline device management, improve security, and enhance overall productivity by providing a centralized platform for managing all endpoints.LEARN MORE ▸
Mobile Device
Management
Our MDM solutions create a hardware environment that saves time, money, and reduces risk. We collaborate with you to create a solution comprised of apps, content, security and device settings of what your team needs without compromising or hindering their experience.
LEARN MORE ▸
Device & Hardware Value Recovery
Gone are the days of selling your devices for pennies on the dollar to a traditional “recycling” or “buy back” company. With optimizing your devices value at the heart of what we do, we’ve created a custom device profit sharing program called The Device Value Optimization Program™.LEARN MORE ▸
Help Desk
Our help desk serves as a centralized point of contact for users within your organization seeking assistance with their IT-related issues, inquiries, or requests. Our help desk is designed to provide efficient and timely support to ensure smooth operation of technology and services.
LEARN MORE ▸
Small Business, Big Security
Affordable Cyber Protection for Your Business
As technology evolves, so do the tactics of malicious actors seeking to exploit vulnerabilities and steal sensitive data. The question is not if, but when your organization will be targeted. The time to bolster your cyber defenses is now.
43% of cyber attacks are aimed at small and medium sized businesses
14% of small and medium sized businesses have cyber protection in place
Small Business, Big Security
Affordable Cyber Protection for Your Business
As technology evolves, so do the tactics of malicious actors seeking to exploit vulnerabilities and steal sensitive data. The question is not if, but when your organization will be targeted. The time to bolster your cyber defenses is now.
43% of cyber attacks are aimed at small and medium sized businesses
14% of small and medium sized businesses have cyber protection in place
Our Commitment to You.


Making The Management of Technology Simpl™.
Making The Management Of Mobile Technology Simpl™.